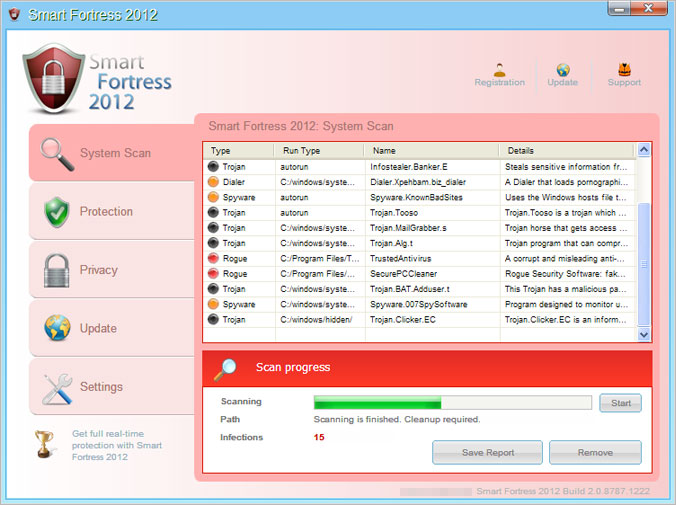
The graphical user interface of Smart Fortress 2012 GUI when it's not registered (trial).
Smart Fortress 2012 GUI when the rogue program is registered (full version).
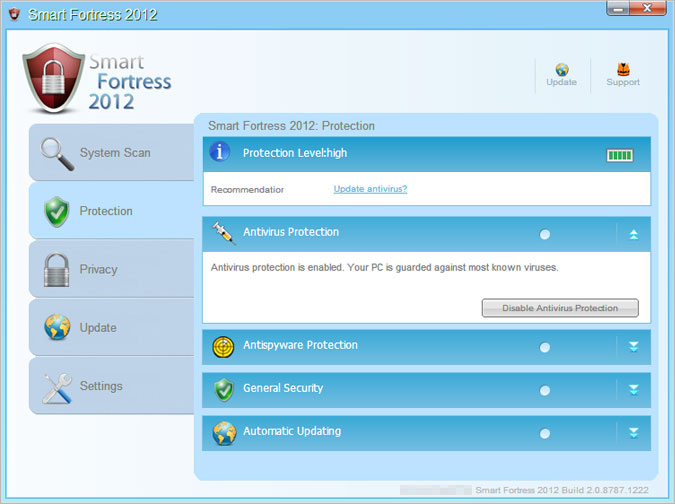
Color is the only difference. It seems that malware authors know color meanings very well. Pink color means danger, infected. Something that requires your attention. Blue means everything is OK. Calm down. Color psychology is a science and it's true that colors effect human behavior.
There are basically two concerns related to rogue anti-virus programs: false sense of security when you think that your computer is bullet proof and protected against the latest malicious code but it's not and identity theft. If you fall victim to a rogue anti-virus program or fraudulent security alert, you should contact your credit card company and dispute the charges. Whoever distributes this malicious program has to keep the number of charge backs as low as possible to be able to stay in the game. Otherwise, they will be banned from the network. Identity thieves may use gathered information for their further malicious activities or simply sell the information on illegal credit card marketplaces. One way or another, it's a huge risk.
Smart Fortress 2012 Version 3.1 is distributed in a numbers of ways, including via infected websites, fake online malware scanners, spam and social engineering. Keep in mind that rogue security programs can get installed on your computer without any interaction from your side. Your computer could be infected simply by visiting an infected website. It's called a 'drive-by download'. This method is very popular among cyber criminals who use exploit kits, mostly BlackHole, to distribute malware. The scheme is very simply - join a rogue AV affiliate network, choose a rogue anti-virus product Smart Fortress 2012 and generate your unique software build. Then you need to buy targeted traffic and you are ready to push some scareware. Thankfully, it's rather difficult to join fake AV affiliate networks nowadays.
Smart Fortress 2012 is probably the most aggressive scareware we've ever seen. It blocks pretty much everything on the compromised computer and constantly displays fake security alerts. It doesn't even allow you to rename its main executable file. You can't open any .exe, .com or .pif file. What is more, the rogue antivirus program stays active in Safe Mode. It basically takes over the whole user account.
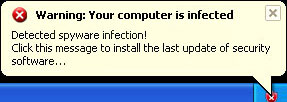
Warning! Your computer is infected - fake balloon notification claiming that your computer is infected with spyware.
Another fake security alert claiming that your machine is infected by a Trojan horse TrojanSPM/LX.
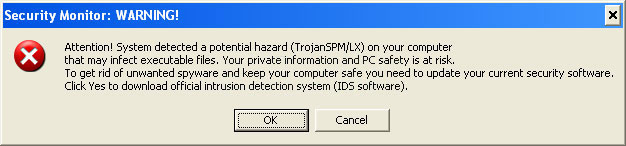
Such fake security alerts may look completely official. It may be very convincing to the unsuspecting users, and the prospect of being infected by Trojans and spyware can be very scary, which is why they may fall victim to this scam.
Smart Fortress 2012 might perform many other activities. It may install additional modules and files to monitor your computer use, install backdoor Trojans and hijack your web browser.
If your computer is infected by Smart Fortress 2012, stop work immediately as this may provide identity thieves with more information about you. To remove Smart Fortress 2012 and associated malware from your computer, please follow the steps in the removal guide below. Some other sites on the internet will probably show you how to remove this virus manually. However, this isn't a good idea. This malware modifies Windows registry and makes some serious changes to your machine that you may not be able to handle properly. If you need extra help removing this virus from your computer, please leave a comment. Good luck and be safe online!
Quick Smart Fortress 2012 removal instructions:
1. Open Smart Fortress 2012 scanner. Click the "Registration" button (top right corner). Enter the following debugged registration key and click "Activate" to register the rogue antivirus program. Don't worry, this is completely legal since it's not genuine software.
AA39754E-715219CE
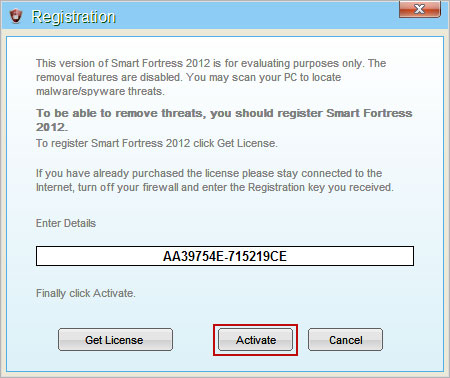
Once this is done, you are free to install recommended anti-malware software and remove Smart Fortress 2012 virus from your computer properly.
2. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
NOTE: don't forget to update anti-malware software before scanning your computer. That's it! Your computer should be virus free.
Tips for avoiding rogue security software:
- Turn on automatic updates. Install all Windows and software updates.
- Install a reliable antivirus program and firewall. Make sure your antivirus program is up to date.
- Use caution when following links on social networks and websites that visit for the first time.
- Use a standard user account instead of an administrator account, especially when visiting suspicious websites or opening potentially harmful files.
- Don't download software from unknown sources.
- Back up your critical files.
Associated Smart Fortress 2012 files and registry values:
Files:
Windows XP:
- C:\Documents and Settings\All Users\Application Data\[SET OF RANDOM CHARACTERS].exe
- C:\ProgramData\[SET OF RANDOM CHARACTERS].exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce "[SET OF RANDOM CHARACTERS]"