Privacy Protection is a rogue antivirus program which allegedly generates false malware warnings saying that your computer is infected with a variety of viruses and spyware. In a common scenario, victim's computer screen is taken over by very annoying security alerts and 'balloon' notifications. The rogue program blocks legitimate security products as well as certain system utilities to evade signature and heuristic detection. Finally, the fake AV says that you need to by the security software in order to remove found viruses and to protect your computer against other sophisticated malware.
Many people have already fell for the ruse by giving their credit card information to cyber crooks. Although, Privacy Protection is not the most sophisticated malware out there, it may cause millions of dollars in damages. The Privacy Protection malware family, which spreads via infected adult websites as well as keygens and file storage services, has been in development for over two years now. The malware is currently in its fifth or sixth version, can't remember exactly because they are very common but the propagation mechanisms wasn't updated, that's for sure. Anyway, if your computer is infected with this virus, please follow the steps in the removal guide below. Privacy Protection
designed to protect is a total scam, do not pay for it!
Here's what the rogue antivirus looks like.

A couple of fake security alerts you may see when this rogue antivirus is active.

Privacy Protection may claim that your web browser or any other problem really, was infected by some form of malware that may send your sensitive information to a remove computer or make your computer unusable, e.g., W32/Blaster.Worm.
iexplore.exe can not start
File iexplore.exe is infected by W32/Blaster.worm
Please activate Malware Protection to protect your computer.

It's worth mentioning, that Privacy Protection may come bundled with the
TDSS rootkit. This malware has the ability to download an array of malicious programs, including spyware, adware, and click fraud bots. You can remove the rogue program manually, but not the rootkit I'm afraid. Removing the rootkit is very important; otherwise it will re-download malicious programs onto your computer after a couple of hours and you will experience system slow downs and fake alerts again. So, to remove Privacy Protection and associated malware from your computer, please follow the removal instructions below. If you have any questions or you need help removing this virus, please leave a comment below. Good luck and be safe online!
http://deletemalware.blogspot.com
Manual Privacy Protection removal instructions:1. Right click on the "Privacy Protection" icon, click
Properties in the drop-down menu, then click the
Shortcut tab.

The location of the malware is in the
Target box.

NOTE: by default, Application Data folder is hidden. Malware files are hidden as well. To see hidden files and folders, please read
Show Hidden Files and Folders in Windows.
Under the Hidden files and folders section, click
Show hidden files and folders, and remove the checkmark from the checkbox labeled:
- Hide extensions for known file types- Hide protected operating system filesClick OK to save the changes. Now you will be able to see all files and folders in the Application Data/Program Data directory.
3. Rename malicious process.
File location, Windows XP:C:\Documents and Settings\All Users\Application Data\privacy.exe
File location, Windows Vista/7:C:\ProgramData\privacy.exe

Rename
privacy.exe to virus.exe or whatever you like. For example:

4. Restart your computer. The malware should be inactive after the restart.
5. Open Internet Explorer and download
TDSSKiller. This malware usually (but not always) comes bundled with TDSS rootkit. Removing this rootkit from your computer is very important (if exists). Run TDSSKiller and remove the rootkit.
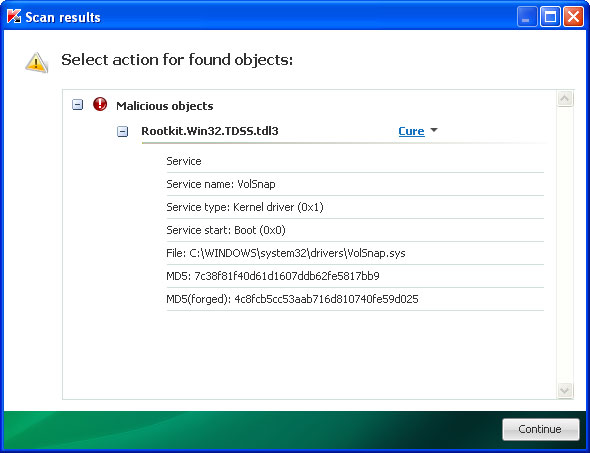
6. And finally, Download recommended
anti-malware software (direct download) and run run a full system scan to remove Privacy Protection from your computer. That's it!
Privacy Protection removal instructions in Safe Mode with Networking:1. Please reboot your computer is "
Safe Mode with Networking". As the computer is booting tap the "
F8 key" continuously which should bring up the "
Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.

NOTE:
Login as the same user you were previously logged in with in the normal Windows mode.
2. Open Internet Explorer and download
TDSSKiller. Run the utility.
3. Then download recommended
anti-malware software (direct download) and run a full system scan to remove this virus from your computer.
Manual activation and Privacy Protection removal:1. Choose to remove threats and manually activate the rogue program. Enter one of the following code
Y76REW-T65FD5-U7VBF5A (and any email) to activate Privacy Protection.
2. Download recommended
anti-malware software (direct download) and run a full system scan to remove this virus from your computer.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to
iexplore.exe or
winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. Remove the TDSS/ZeroAccess rootkit (if exists). Please follow this removal guide:
http://deletemalware.blogspot.com/2010/03/tdss-alureon-tidserv-tdl3-removal.html
Privacy Protection associated files and registry values:Files:
- C:\Documents and Settings\All Users\Application Data\privacy.exe
Registry values:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Privacy Protection"
Share this information with other people:



















