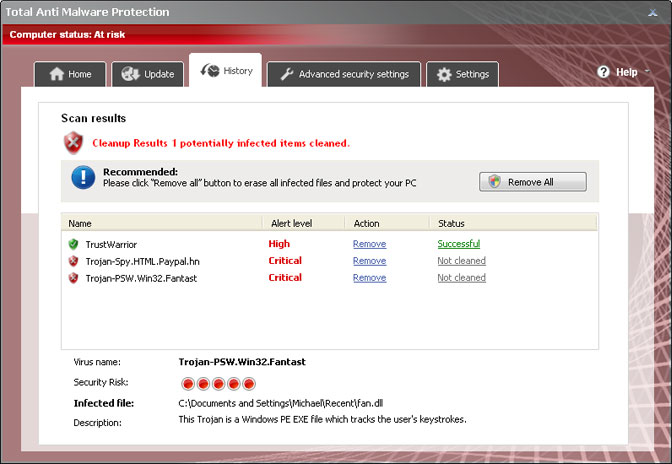
To make things worse, Total AntiMalware Protection overwrites Windows Hosts file. It adds some additional code lines that will eventually cause web browser redirection to findgala.com and some other sites that seem to be among the less clean ones in terms of keeping out the malware links. Again, you can't just simply edit Hosts file and remove code lines that are not supposed to be there because the rogue program sets new file permissions that basically say "You are not allowed to change it". Thankfully, Microsoft has this great utility called "Fix it" that gets things done very easily, so you don't need to mess up with Windows permissions.
If your computer has been infected with Total Anti Malware Protection, please follow the steps the removal guide below. Whatever you do, DO NOT pay for it. Total Anti Malware Protection is a scam. Once you give you money to scammers you won't be able to get them back. No 30 day money back guarantee, sorry. Also, you should re-evaluate your protective measures: run non-admin, keep patches up-to-date, and don't run e-mailed executables. If you have any questions, please leave a comment below. Safe surfing folks!
Update (May 7, 2012): Scammers have slightly modified the GUI and changed the name of this rogue anti-spyware program. Now it's called Best Antivirus Software. Of course, there still might be some actively distributed variants of Total AntiMalware Protection and as a matter of fact we believe that they pushes different rogues simultaneously. Anyway, the removal guide outlined below works just fine for both variants of this rogue anti-spyware program.
Total Anti Malware Protection removal guide:
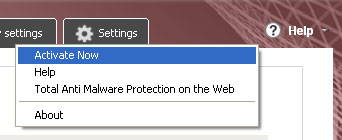
1. Click on Help and select Activate Now.
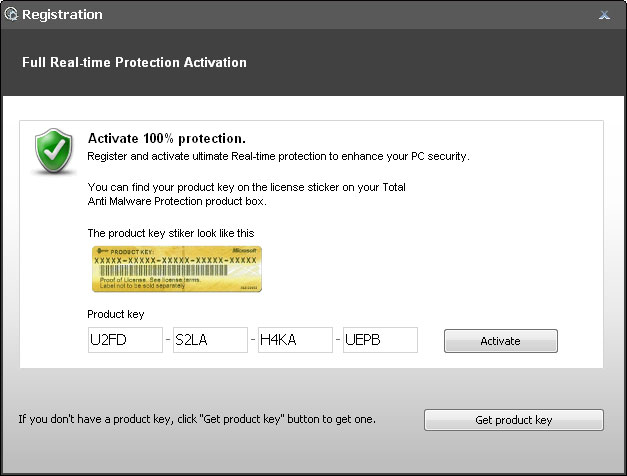
2. Enter one the following debugged registration keys and click Activate to register the rogue antivirus program. Don't worry, this is completely legal since it's not genuine software.
U2FD-S2LA-H4KA-UEPB
K7LY-H4KA-SI9D-U2FD
K7LY-R5GU-SI9D-EVFB
2. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this malware from your computer.
3. To reset the Hosts file back to the default automatically, download and run Fix it and follow the steps in the Fix it wizard.
Source: http://deletemalware.blogspot.com
Associated Total Anti Malware Protection files and registry values:
Files:
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS]\[SET OF RANDOM CHARACTERS]
- %AppData%\Total Anti Malware Protection\
- %AppData%\Microsoft\Internet Explorer\Quick Launch\Total Anti Malware Protection.lnk
- %UserProfile%\Desktop\Total Anti Malware Protection\
- %UserProfile%\Start Menu\Total Anti Malware Protection\
- %UserProfile%\Start Menu\Programs\Total Anti Malware Protection.lnk
- HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Run\Total Anti Malware Protection = "%AllUsersProfile%\Application Data\a2r3fq\FPa1a_7294.exe" /s /d
- HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\[RANDOM].exe\Debugger = svchost.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun = 01000000
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun\[1...15]
No comments:
Post a Comment