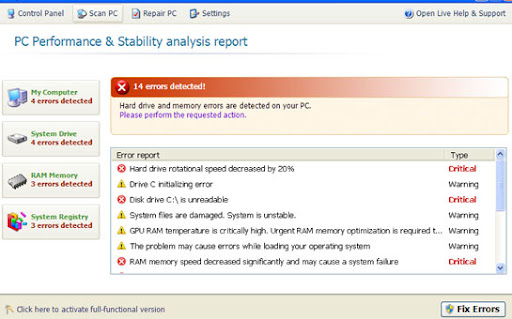
Security Monitor 2012 is a rogue anti-virus program that mimics genuine security software and gives false warnings about viruses. What's the aim of this malware? To make you think that your computer is infected with spyware and other bad stuff and to trick you into paying for bogus software. In other words, to make tons of money for cyber criminals. It's a clone of Security Solution 2011, so it's not a new rogue anti-virus but just a slightly modified old one. I could go on and on about this little nasty bug... But I will stick to the facts because I haven't bought Christmas gifts yet and I'm running out of time.
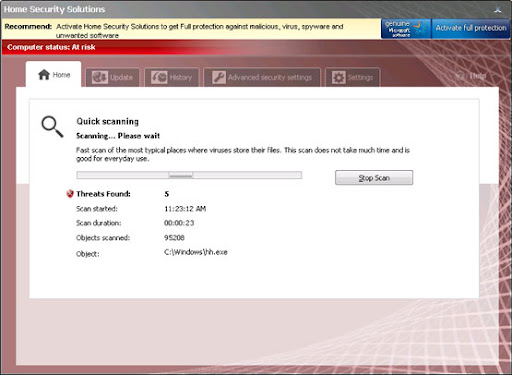
So, Security Monitor 2012 mainly relies on social engineering or fraud and software vulnerabilities. It has to be manually installed but in some cases it can be dropped on the system by Trojan downloaders and similar malware. Update your software! Once installed, Security Monitor 2012 pretends to scan your computer for viruses, spyware and Trojans. Of course, it finds numerous critical infections. Why I'm not surprised? It's constantly asking to buy anti-virus software from securitymonitor2012.com which then redirects users to a payment processor onlinestarpayment.com. DON'T buy it! If you've been hit by this rogue antivirus program, please follow the instructions below to remove Security Monitor 2012 and regain control of your computer again.

Security Monitor 2012 blocks the execution of other programs, mainly Windows system utilities and genuine anti-virus software, by saying they are infected.
Security Monitor 2012
The application mspaint.exe was launched successfully but it was forced to shut down due to security reasons. This application infected by a malicious software program which might present damage for the PC. It is highly recommended to make a full scan of your computer to exterminate the malicious programs from it.
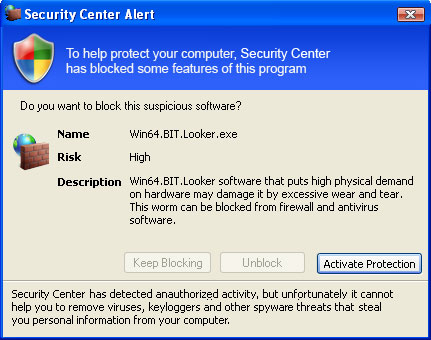
The only exception is Internet Explorer. You can still open it. Apparently, they don't want to block the way so that you can purchase their bogus software. It also displays a fake Windows Security Center alert saying that your computer is infected with Screen.Grab.J.exe or Win64.BIT.Looker.exe.
Security Monitor 2012 will also infect your Task Manager and will not allow you to run Windows updates. So, as I said, it's truly annoying bug. Thankfully, it's not as dangerous as banking Trojans and spyware.
You can remove Security Monitor 2012 using anti-malware software (recommended) or manually but I'm not sure this is a permanent fix. So, just enter the cracked reg key given below. The rogue program won't block anti-malware software anymore. Then download recommend anti-malware software and run a full system scan. This is quick and effective. If you choose to remove it manually, I'm here to help you. Just leave a comment below if you need extra help. Last, but not least, if you've already paid for it, please contact your credit card company immediately and dispute the charges. Good luck and be safe online! Marry X-mas everybody ;-)
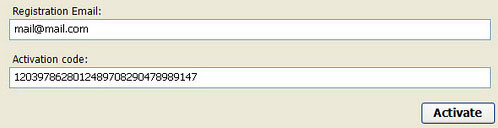
Quick removal guide:1. Update: You can use this cracked serial key
LIC2-00A6-234C-B6A9-38F8-F6E2-0838-F084-E235-6051-18B3 to register the fake antivirus in order to stop the fake security alerts. Just click the
Activate button and enter the reg key manually. Don't worry, this is completely legal.
Once this is done, you are free to install anti-malware software and remove the rogue anti-virus program from your computer properly.
2. Download recommended
anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
Alternate Security Monitor 2012 removal instructions:1. Download recommended
anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
If you can't download it, please reboot your computer is "
Safe Mode with Networking". As the computer is booting tap the "
F8 key" continuously which should bring up the "
Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Open Internet Explorer and download STOPzilla. Once finished, go back into
Normal Mode and run it. Don't run STOPzilla in Safe Mode! That's It!
Read more detailed instructions here:
http://www.computerhope.com/issues/chsafe.htm
NOTE:
Login as the same user you were previously logged in with in the normal Windows mode.
Security Monitor 2012 removal instructions using HijackThis or Process Explorer (in Normal mode):1. Download
iexplore.exe (NOTE: iexplore.exe file is renamed
HijackThis tool from TrendMicro).
Launch the iexplore.exe and click "Do a system scan only" button.
If you can't open iexplore.exe file then download
explorer.scr and run it.
2. Search for such entry in the scan results:
O4 - HKCU\..\Run: [Security Manager] C:\Documents and Settings\[User Name]\Application Data\Security Monitor\securitymanager.exeO4 - HKCU\..\Run: [Security Monitor 2012] "C:\Documents and Settings\[User Name]\Application Data\Security Monitor\Security Monitor.exe" /STARTUPSelect all similar entries and click once on the "Fix checked" button. Close HijackThis tool.
OR you can download
Process Explorer and end Security Monitor 2012 processes:
- Security Monitor.exe
- securitymanager.exe
- securityhelper.exe
3. Download recommended
anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to
iexplore.exe,
explorer.exe or
winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
Associated Security Monitor 2012 files and registry values:Files:
In Windows XP:
- C:\Documents and Settings\[UserName]\Application Data\Security Monitor\
- C:\Documents and Settings\[UserName]\Application Data\Security Monitor\Security Monitor.exe
- C:\Documents and Settings\[UserName]\Application Data\Security Monitor\securitymanager.exe
- C:\Documents and Settings\[UserName]\Application Data\Security Monitor\securityhelper.exe
In Windows Vista/7:
- C:\Users\[UserName]\AppData\Roaming\Security Monitor\
- C:\Users\[UserName]\AppData\Roaming\Security Monitor\Security Monitor.exe
- C:\Users\[UserName]\AppData\Roaming\Security Monitor\securitymanager.exe
- C:\Users\[UserName]\AppData\Roaming\Security Monitor\securityhelper.exe
Registry values:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\Security Monitor
- HKEY_CURRENT_USER\Software\Security Monitor
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Security Monitor"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Security Monitor 2012 Security"
Share this information with other people: