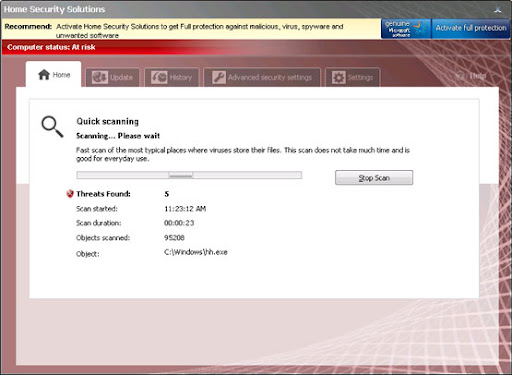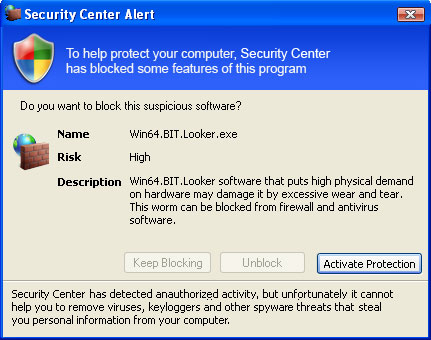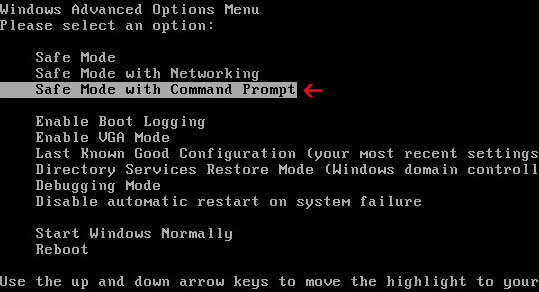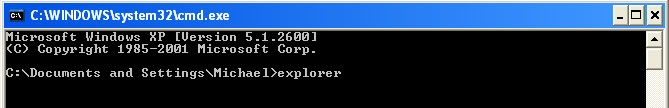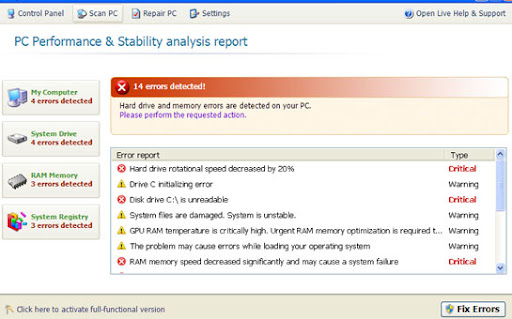
Common symptoms of System Check infection:
- false error messages, "Hard drive clusters are partly damaged" and similar
- all icons and shortcuts are gone
- Task Manager and other system utilities are blocked
- can't run anti-virus software
- search results page got redirected to irrelevant and infected websites. Happens in Internet Explorer and Mozilla Firefox.
- rosedalolandou.com
- ushbrenerw.net

Don't blame yourself if you fell for this scam. Call your credit card company and dispute the charges. Then follow the steps in the removal guide below to remove System Check and associated malware from your computer. If you have any questions, please leave a comment below. Good luck and be safe online!
Quick removal:
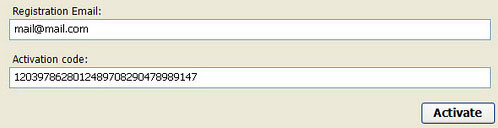
1. Use debugged registration key and fake email to register System Check malware. This will allow you to download and run any malware removal tool you like and restore hidden files and shortcuts. Choose to activate "System Check" manually and enter the following email and activation code:
mail@mail.com
15801587234612645205224631045976 (new code!)
mail@mail.com
1203978628012489708290478989147 (old code, may not work anymore)
2. Download TDSSKiller and run a system scan. Remove found rootkits as shown in the image below. Reboot your computer if required.
3. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
Alternate System Check removal instructions:
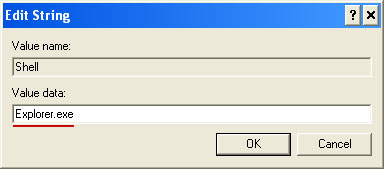
1. Open Internet Explorer. If the shortcut is hidden, pelase Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter iexplore.exe and hit Enter or click OK.

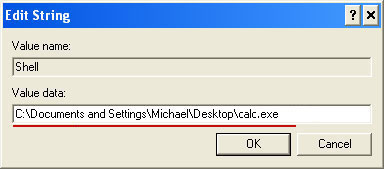
2. Download and run this utility to restore missing icons and shortcuts.
3. Now, please download TDSSKiller and run a system scan. Remove found rootkits as shown in the image below. Reboot your computer if required.

Please note that your computer might be rootkit free, not all version of System Check comes bundled with rootkits. Don't worry if TDSSKiller didn't find a rootkit.
4. Finally, download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
5. System Check virus should be gone. If certain icons and shortcuts are still missing, please use restoresm.zip.
Associated System Check files and registry values:
Files:
Windows XP:
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Start Menu\Programs\System Check\
%UserProfile% refers to: C:\Documents and Settings\[User Name]
Windows Vista/7:
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Start Menu\Programs\System Check\
%UserProfile% refers to: C:\Users\[User Name]
Registry values:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS].exe"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = 'yes'