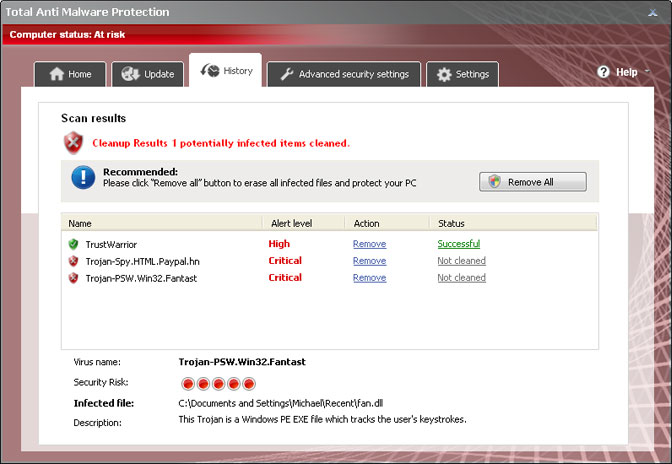
Shortly after we ran a certain set of Trojans on our test machine, we found a sample (Trojan.Small.dac or Troj/RuinDl-Gen) that was responsible for the combination of the Recommended for You pop-ups and web browser redirects. The web browser redirects seem to happen at random or at least they didn't happen all the time. The Trojan horse displayed two different pop-up windows: an iPhone looking box with various advertisements and a smaller one with just random ads. It happened in Internet Explorer, Mozilla Firefox and Google Chrome. Can't blame the browser this time. It's probably a cross platform malware too. Besides, it happened on both 32-bit and 64-bit systems. Ads were not very intrusive, they didn't show up like every two or five minutes. Once you minimize the ad box, it doesn't appear until you restart your computer. That's right, you can't close the ad box, when you click the "X" it just minimizes into a smaller box that says "Recommended for You".
An-iPhone looking ad box:

A smaller one, but still very annoying:

Recommended for You box:

Now, that we know the root of this problem (malware) we can take the appropriate actions. Running a full virus scan with anti-malware software is essential step towards solving the Recommended for You malware problem. Once the Trojan horse is gone, you need to replace Windows Host file since it's partly responsible for web browser redirects and annoying pop-ups as well. Yes, the Trojan modifies Windows Hosts file making web browser inquiries a subject to redirect. To remove this malware from your computer, please follow the steps in the removal guide below. Should you need any further assistance, don't hesitate to contact us or just leave a comment below. Good luck and be safe online!
http://deletemalware.blogspot.com
Recommended for You malware removal instructions:
1. Download recommended anti-malware software (direct download) and run a full system scan to remove this malware from your computer.
3. To reset the Hosts file back to the default automatically, download and run Fix it and follow the steps in the Fix it wizard.
4. Remove files from Windows %Temp% folder.
Tell your friends: