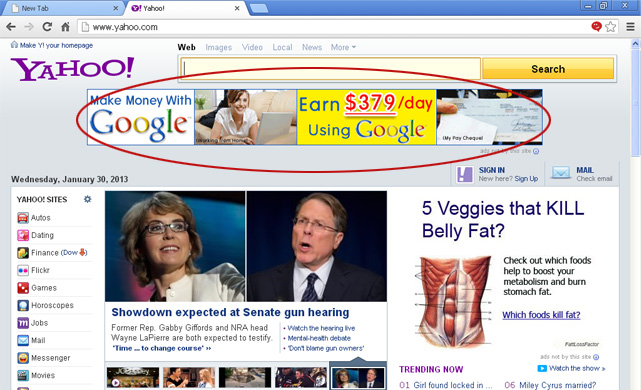
An advertisement displayed on Yahoo! front page that leads to 'work at home' scam page even though it mentions Google, the ad redirects users to a rogue website. I'm sure ads on Yahoo! front page are very expensive even if they are served for a short period of time. However, apparently cyber criminals decided to invest money into malicious web browser extensions instead of spending them on expensive ads.
Here's another example, Ads not by this site ads are pushing Google search results and paid ads below the fold. They even use the same colors and text size to mislead users into thinking that these are Google ads. Since most users use and trust Google search engine I truly believe that click through rate is fairly high.
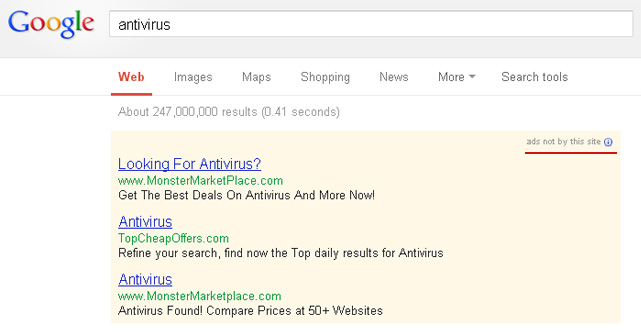
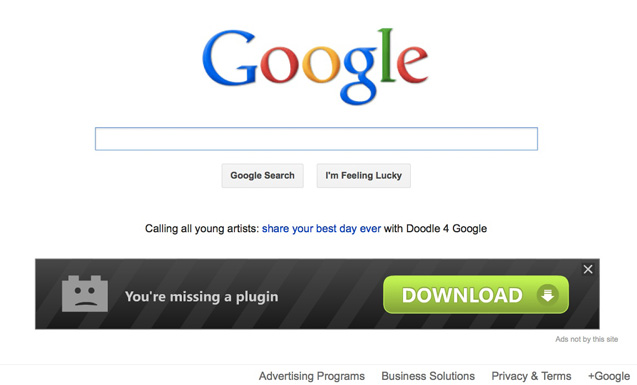
I saved the best example for last. Here it is, an ad displayed on Google search front page, claiming that you are missing a plug-in. No comment needed :)
Web browser extensions that inject "Ads not by this site" advertisements are very often distributed through various deceptive practices. BHOs can take a form of browser toolbars but from what I've seen so far they just take over your web browser homepage and default search engine. Such malicious extensions or so-called web browser hijackers come bundled with other software. There's even a term foistware which is used to describe software that is installed on your computer without your knowledge. Cyber criminals use silent and delayed installers as well as Trojan downloaders to install malicious software on your computer. Besides, even if they add checkboxes and ostensibly allow you to skip toolbar installation, there are many not so technically savvy users who do not understand that a "recommended" toolbar isn't that great after all. Or that it will even inject ads on websites that do not serve them, for example Wikipedia.
Cyber criminals simply want to turn visitors into customers. They could even serve malicious ads that might lead to infected websites and exploit kits. So, it's not only unethical but also very dangerous. That's why I highly recommend you to remove malicious web browser extensions and BHOs that cause Ads not by this site banners to show up on your computer screen. There are numerous Ads not by this site associated programs and extensions. I listed them below and I promise to update the list whenever I find something new. In short, remove all recently installed applications and web browser extensions or those that were installed without your knowledge. Some of them may be protected; the Remove button is simply grayed out. In such case, uninstall the application that installed the malicious web browser extension. For example, CouponDropDown, I want This!, BCool App, SaveAs, Vid Saver, Save Now 3.5 or Coupon Companion. Find the complete list below. This web page contains a step-by-step guide on how to remove "Ads not by this site" virus from Internet Explorer, Mozilla Firefox, Google Chrome and Apple Safari.
And finally, to avoid web browser hijacking, use real-time anti-malware software and don't give unknown websites permission to install such toolbars and extensions as "Ads not by this site". Post your comment or question below. Good luck and be safe online!
Remove Ads not by this site associated applications:
1. First of all, download recommended anti-malware software and run a full system scan. It will detect and remove this infection from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this browser hijacker. Hopefully you won't have to do that.
2. Remove "Ads not by this site" from your computer using the Add/Remove Programs control panel (Windows XP) or Uninstall a program control panel (Windows 7 and Windows 8).
Go to the Start Menu. Select Control Panel → Add/Remove Programs.
If you are using Windows Vista or Windows 7, select Control Panel → Uninstall a Program.
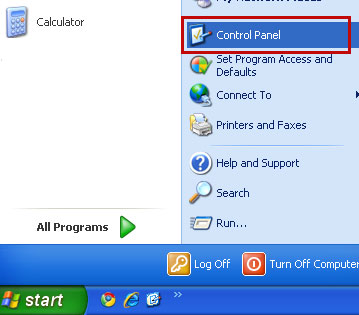
If you are using Windows 8, simply drag your mouse pointer to the right edge of the screen, select Search from the list and search for "control panel".

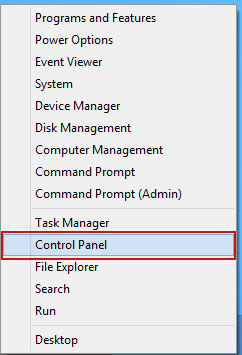
Or you can right-click on a bottom left hot corner (formerly known as the Start button) and select Control panel from there.
3. When the Add/Remove Programs or the Uninstall a Program screen is displayed, scroll through the list of currently installed programs and remove the following entries (if exist):
|
|
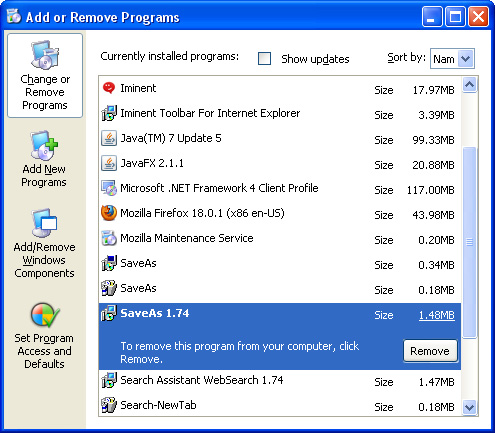
Simply select each application and click Remove. If you are using Windows Vista, Windows7 or Windows 8, click Uninstall up near the top of that window. When you're done, please close the Control Panel screen.
Remove Ads not by this site from Google Chrome:
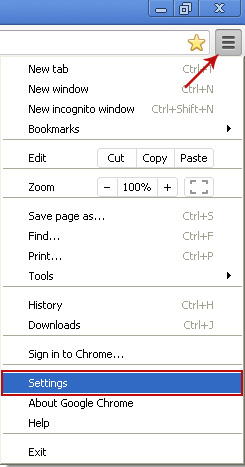
1. Click on Chrome menu button. Go to Tools → Extensions.
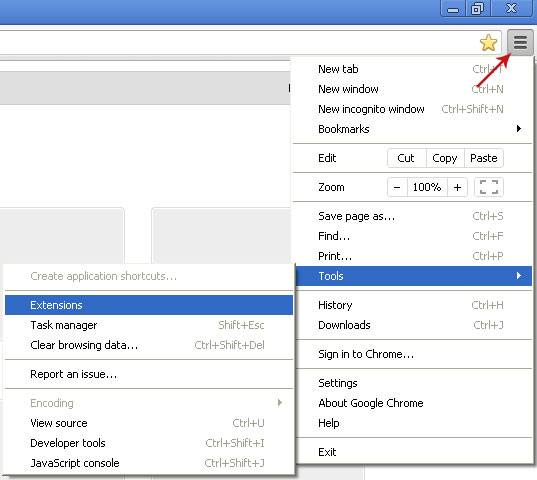
2. Click on the trashcan icon and remove the extensions listed above if they are present:
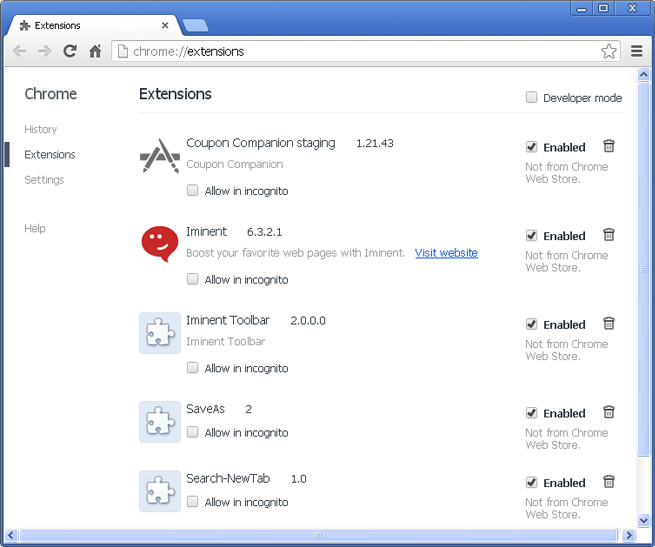
Once you have found and removed all of the above extensions that were installed on your computer, you can close Google Chrome. Please note, that some extensions might be locked (remove option is disabled). In such case, you have to remove those extensions manually. Enable Developer Mode to find extension's name that go to Google Chrome extension folder and delete it. Google Chrome extension folder placed in the following directory:
Windows 7 → C:\Users\[UserName]\AppData\Local\Google\Chrome\User Data\Default\Extensions
Windows XP → C:\Documents and Settings\[UserName]\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions
Remove Ads not by this site from Mozilla Firefox:
1. Open Mozilla Firefox. Go to Tools → Add-ons.
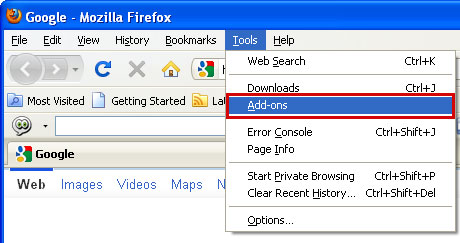
2. Select Extensions. If any of the extensions listed above exist, click on the Remove button next to each one. If you can't find the Remove button, then simply click on the Disable button.
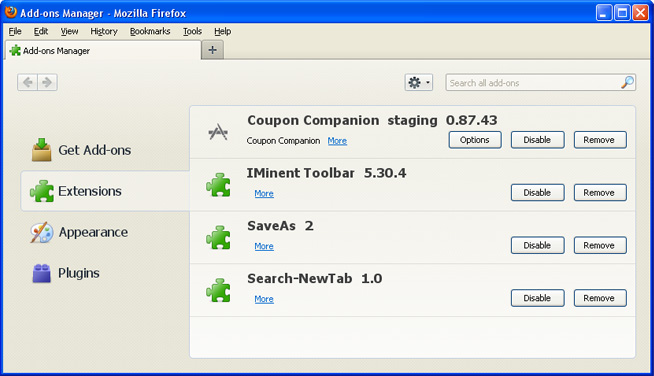
Once you have found and removed all of the above extensions that were installed on your computer, you can close Mozilla Firefox. Disabling a web browser extension might also help, however, it still exists on your PC. Some extensions might be blocked or only have an option to disable them. In such case, I recommend you to delete extensions manually.
Remove Ads not by this site from Internet Explorer:
1. Open Internet Explorer. Go to Tools → Manage Add-ons. If you have the latest version, simply click on the Settings button.
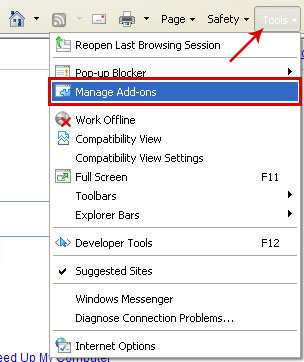
2. Select Toolbars and Extensions. If any of the extensions listed above exist, select it and then click on the Remove/Disable button to remove it from Internet Explorer.
Once you have removed/disabled all of the above extensions (if existed), you can close Internet Explorer.

Remove Ads not by this site from Apple Safari:
1. Open Safari. Go to Preferences.
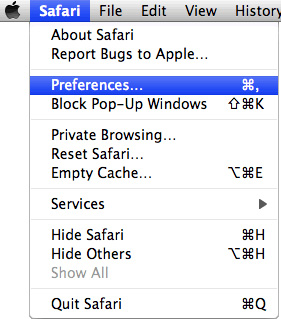
2. Select the Extensions tab. If any of the extensions listed above exist, select it and then click on the Uninstall button to remove it from Apple Safari.
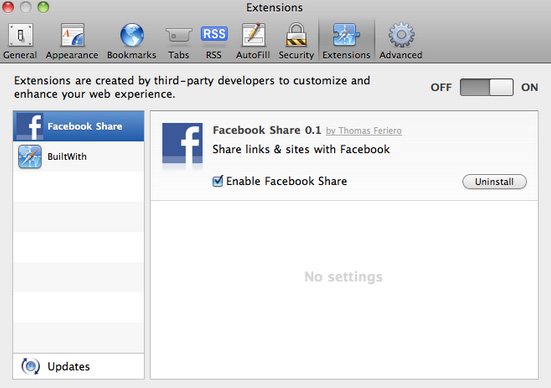
Once you have removed all of the above extensions (if existed), you can close Apple Safari.
Tell your friends: