This rogue program goes by many different program names listed below.
- XP Antispyware
- XP Antispyware 2011
- XP Anti-Virus
- XP Anti-Virus 2011
- XP Total Security
- XP Total Security 2011
- XP Security
- XP Security 2011
- XP Internet Security
- XP Internet Security 2011
- XP Antimalware
- XP Antimalware 2011
- XP Guard
- XP Home Security 2011
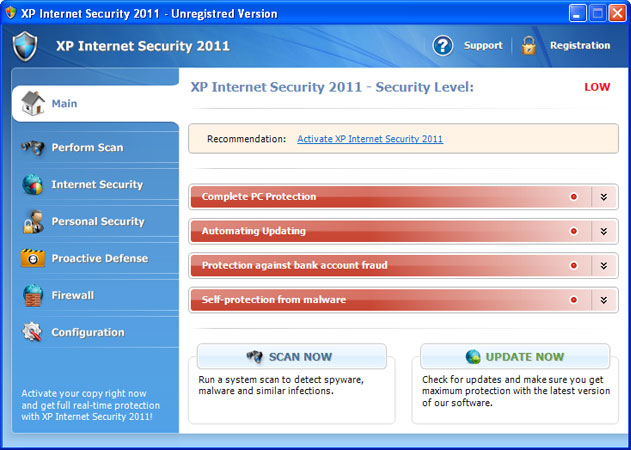
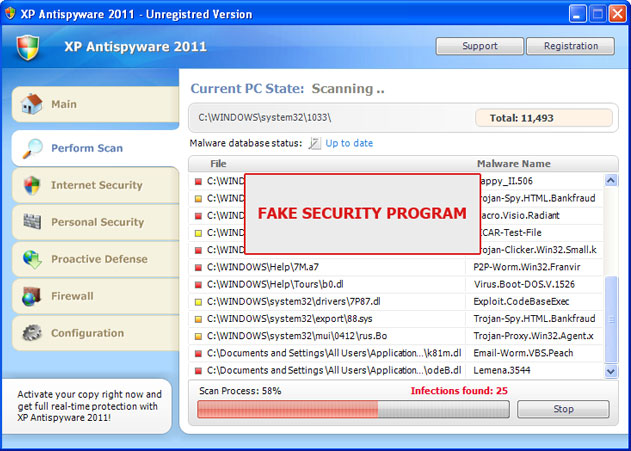
While XP Antispyware 2011 is running, it will pretend to scan your computer for malicious code. Obviously, it will find numerous infections, e.g. e-mail worms, trojans, spyware and other malicious software on your computer. Then it will ask you to pay for a full version of the program to remove the infections which do not even exist. Please do not fall victim to this scam. As a typical rogue, XP Antispyware 2011, XP Security or any other other name, will display fake security warnings and notification from your Windows taskbar. The text of some of the fake alerts is:
System danger!
Your system security is in danger. Privacy threats detected. Spyware, keyloggers or Trojans may be working the background right now. Perform an in-depth scan and removal now, click here.
Stealth intrusion!
Infection detected in the background. Your computer is now attacked by spyware and rogue software. Eliminate the infection safely, perform a security scan and deletion now.
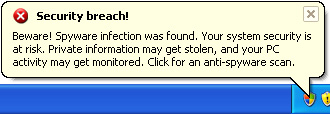
Privacy threat!
Spyware intrusion detected. Your system is infected. System integrity is at risk. Private data can be stolen by third parties, including credit card details and passwords. Click here to perform a security repair.
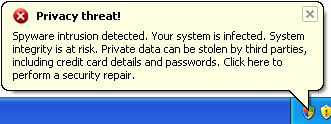
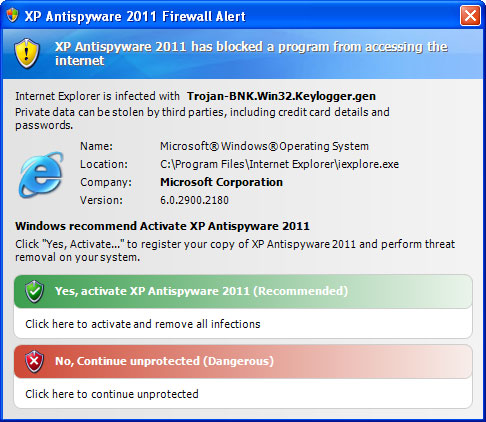
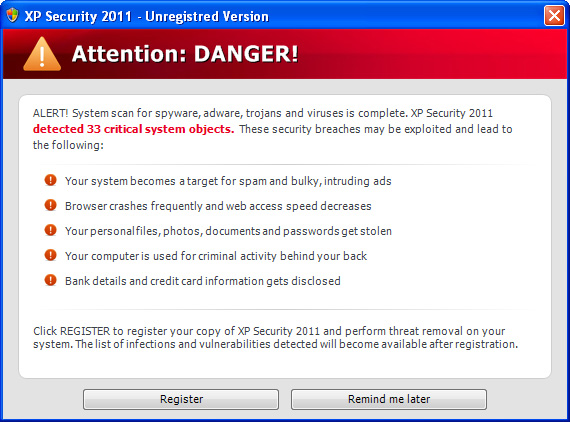
So, as you can see, the rogue program does all its best to scare you into thinking that your computer is infected with spyware, trojans and other viruses. It will even claim that your sensitive information will be stolen and sold. Don't worry, all these alerts are fake. You just need to remove the rogue program and maybe some related malware from your computer and you will be good to go. XP Antispyware 2011 or XP Guard will also hijack Intenet Explorer and Mozilla Firefox. The problem is that you won't be able to download malware removal software. The rogue program will display a fake alert that the site you are visiting is dangerous. Of course, that’s not true. The fake message reads:
Internet Explorer alert. Visiting this site may pose a security threat to your system!
Possible reasons include:
- Dangerous code found in this site's pages which installed unwanted software into your system.
- Suspicious and potentially unsafe network activity detected.
- Spyware infections in your system
- Complaints from other users about this site.
- Port and system scans performed by the site being visited.
Things you can do:
- Get a copy of XP Antispyware 2011 to safeguard your PC while surfing the web (RECOMMENDED)
- Run a spyware, virus and malware scan
- Continue surfing without any security measures (DANGEROUS)
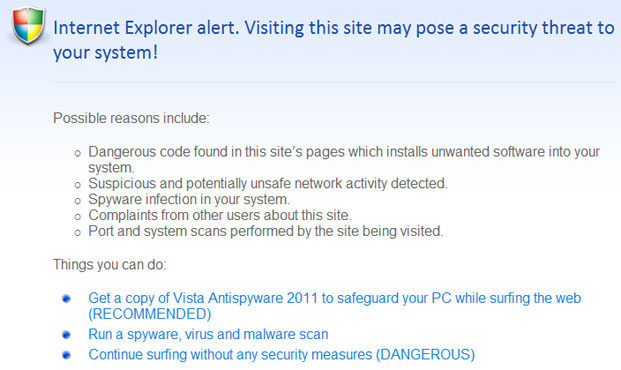
Last, but not least, XP Antispyware 2011 will block certain programs on your computer. So, first of all you will have to stop the rogue program and fix the registry. If your PC is heavily you will need to use a different computer than the infected one to download and transfer all the necessary files required to remove the rogue program. By the way, if you have already purchased this bogus program then you should contact your credit card company and dispute the charges or even cancel your credit card. Then please follow the removal instructions below. If you have any questions or additional information about XP Antispyware 2011, XP Guard or XP Internet Security 2011, please leave a comment. Good luck and be safe online!
XP Antispyware 2011, XP Guard, XP Internet Security 2011 removal instructions:
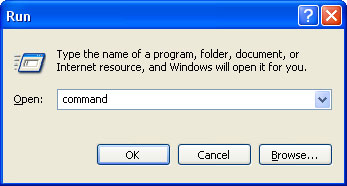
1. Click Start->Run or press WinKey+R. Type in "command" and press Enter key.
2. In the command prompt window type "notepad" and press Enter key. Notepad will come up.
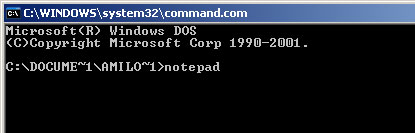
3. Copy all the text in blue color below and paste to Notepad.
Windows Registry Editor Version 5.00
[-HKEY_CURRENT_USER\Software\Classes\.exe]
[-HKEY_CURRENT_USER\Software\Classes\secfile]
[-HKEY_CLASSES_ROOT\secfile]
[-HKEY_CLASSES_ROOT\.exe\shell\open\command]
[HKEY_CLASSES_ROOT\exefile\shell\open\command]
@="\"%1\" %*"
[HKEY_CLASSES_ROOT\.exe]
@="exefile"
"Content Type"="application/x-msdownload"
4. Save file as fix.reg to your Desktop. NOTE: (Save as type: All files)
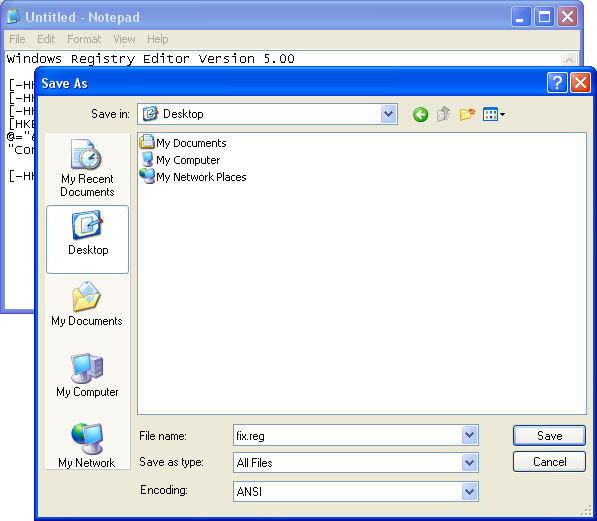
5. Double-click on fix.reg file to run it. Click "Yes" for Registry Editor prompt window. Then click OK.
6. Download recommended anti-malware software (direct download) from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
7. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET NOD32.
Alternate removal instructions:
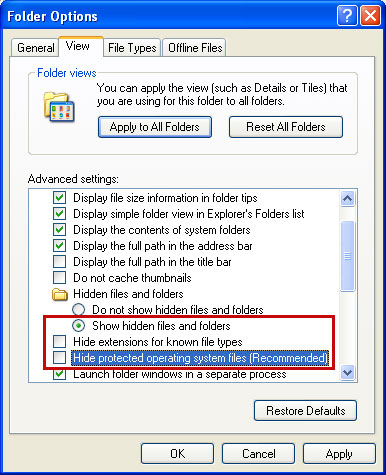
Make sure that you can see hidden and operating system protected files in Windows. For more in formation, please read Show Hidden Files and Folders in Windows.
Under the Hidden files and folders section, click Show hidden files and folders, and remove the checkmarks from the checkboxes labeled:
- Hide extensions for know file types
- Hide protected operating system files
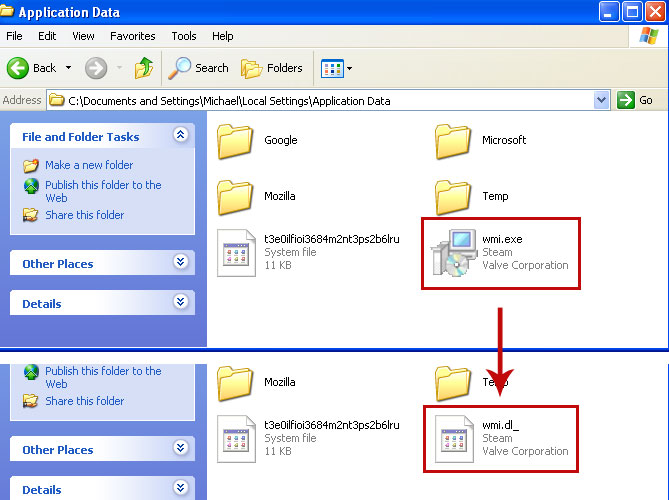
1. Go into C:\Documents and Settings\[UserName]\Local Settings\Application Data\ folder.
For example: C:\Documents and Settings\Michael\Local Settings\Application Data\
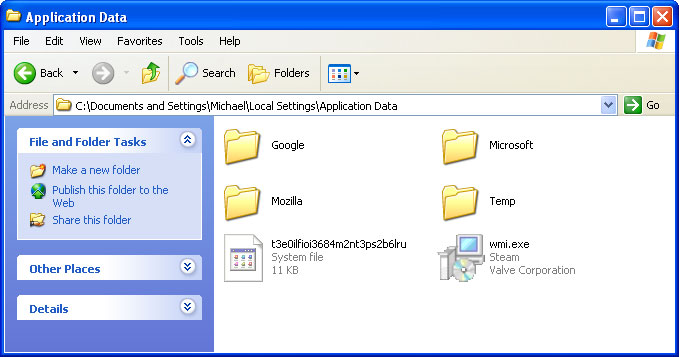
2. Find hidden executable file in this folder. In our case it was called wmi.exe, but I'm sure that the file name will be different in your case. Rename wmi.exe to wmi.dl_ and click Yes to confirm file rename. Then restart your computer.
3. After a restart, open Internet Explorer. Download xp_exe_fix.reg and save it to your Desktop. Double-click on xp_exe_fix.reg to run it. Click "Yes" for Registry Editor prompt window. Click OK.
4. Download recommended anti-malware software (direct download) from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
5. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET NOD32.
Associated XP Antispyware 2011, XP Guard, XP Internet Security 2011 files and registry values:
Files:
- C:\Documents and Settings\All Users\[SET OF RANDOM CHARACTERS]
- C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS]
- C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe
- C:\Documents and Settings\[UserName]\Templates\[SET OF RANDOM CHARACTERS]
- C:\Documents And Settings\[UserName]\Local Settings\Temp\[SET OF RANDOM CHARACTERS]
Registry values:
- HKEY_CURRENT_USER\Software\Classes\.exe "(Default)" = 'exefile'
- HKEY_CURRENT_USER\Software\Classes\.exe "Content Type" = 'application/x-msdownload'
- HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon "(Default)" = '%1' = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" /START "%1" %*'
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "IsolatedCommand" = '"%1" %*'
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "(Default)" = '"%1" %*'
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "IsolatedCommand" = '"%1" %*'
- HKEY_CURRENT_USER\Software\Classes\exefile "(Default)" = 'Application'
- HKEY_CURRENT_USER\Software\Classes\exefile "Content Type" = 'application/x-msdownload'
- HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon "(Default)" = '%1'
- HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" /START "%1" %*'
- HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "IsolatedCommand" = '"%1" %*'
- HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "(Default)" = '"%1" %*'
- HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "IsolatedCommand" - '"%1" %*'
- HKEY_CLASSES_ROOT\.exe\DefaultIcon "(Default)" = '%1'
- HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" /START "%1" %*'
- HKEY_CLASSES_ROOT\.exe\shell\open\command "IsolatedCommand" = '"%1" %*'
- HKEY_CLASSES_ROOT\.exe\shell\runas\command "(Default)" = '"%1" %*'
- HKEY_CLASSES_ROOT\.exe\shell\runas\command "IsolatedCommand" = '"%1" %*'
- HKEY_CLASSES_ROOT\exefile "Content Type" = 'application/x-msdownload'
- HKEY_CLASSES_ROOT\exefile\shell\open\command "IsolatedCommand" = '"%1" %*'
- HKEY_CLASSES_ROOT\exefile\shell\runas\command "IsolatedCommand" = '"%1" %*'
- HKEY_CLASSES_ROOT\exefile\shell\open\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" /START "%1" %*'
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe"'
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode'
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" /START "C:\Program Files\Internet Explorer\iexplore.exe"'
No comments:
Post a Comment