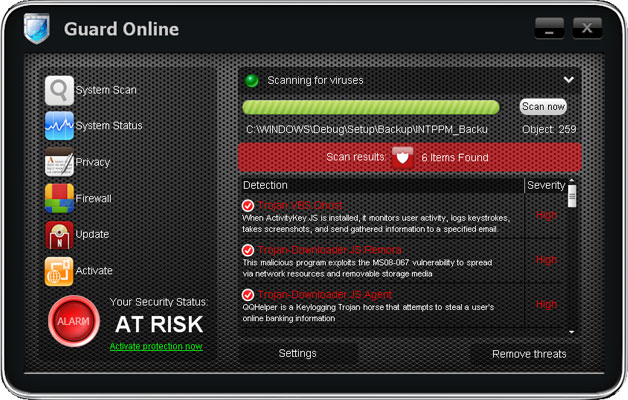
But that's not all, cyber criminals decided that it would be a lot better to drop a rootkit from the notorious TDSS malware family to make the removal procedure a lot more complicated. To remove Guard Online from your computer, please follow the removal instructions below. Although, the removal guide was originally created to help you to remove the AV Guard Online scareware, this guide identifies the procedures to be followed to ensure appropriate Guard Online removal as well. If you have any questions, please leave a comment below. Good luck and be safe online!
http://deletemalware.blogspot.com
Guard Online removal instructions:
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. Remove the TDSS rootkit (if exists). Please follow this removal guide: http://deletemalware.blogspot.com/2010/03/tdss-alureon-tidserv-tdl3-removal.html
Manual Guard Online removal guide:
1. Right-click on Guard Online icon and select Properties. Then select Shortcut tab.
The location of the malware is in the Target box.
2. In our case the malicious file was located in C:\Windows\System32 folder. Select the malicious file, rename it and change a file name extension.
Original file: TcS22bF3nGaQWKf.exe

Renamed file: TcS22bF3nGaQWKf.vir

3. Restart your computer. After a reboot, download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. Remove the TDSS rootkit (if exists). Please follow this removal guide: http://deletemalware.blogspot.com/2010/03/tdss-alureon-tidserv-tdl3-removal.html
Manual activation and Guard Online removal:
1. Choose to remove threats and manually activate the rogue program. Enter one of the following codes to activate AV Guard Online.
9992665263
1148762586
1171249582
1186796371
1196121858
1225242171
1354156739
1579859198
1789847197
1835437232
1837663686
1961232582
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. Remove the TDSS rootkit (if exists). Please follow this removal guide: http://deletemalware.blogspot.com/2010/03/tdss-alureon-tidserv-tdl3-removal.html
Associated Guard Online files and registry values:
Files:
- C:\WINDOWS\system32\[SET OF RANDOM CHARACTERS].exe
- C:\Documents and Settings\[UserName]\Application Data\csrss.exe
- C:\Documents and Settings\[UserName]\Application Data\hTrkd58DeORldrQGuard Online.ico
- C:\Documents and Settings\[UserName]\Application Data\Microsoft\csrss.exe
- C:\Documents and Settings\[UserName]\Desktop\Guard Online.lnk
- C:\Documents and Settings\[UserName]\Local Settings\Temp\[SET OF RANDOM CHARACTERS].tmp
- C:\Documents and Settings\[UserName]\Start Menu\Programs\Guard Online\Guard Online.lnk
Registry values:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS]"
No comments:
Post a Comment