The worst part is that it hijacks a compromised computer, intentionally misrepresents the system status and asks user to pay for bogus PC repair software activation to remove non-existing hard drive errors and other risks from the computer. Unlike ransomware, it doesn’t freeze your computer screen (thanks for that). But it does perform actions that prevent user from accessing certain applications and Windows features. In rare cases, it can make computer unstable forcing unexpected reboots and blue screens of death.
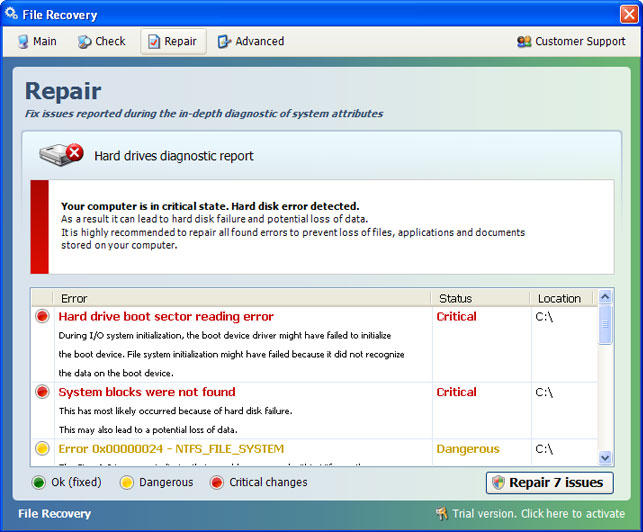
If you pay for this rogue application you will lose your money and probably without a chance to get them back. But you can still contact your credit card company and dispute the charges. Who knows it might just work. After all, you don’t have anything to lose. At least you know it’s a scam. Besides, more than 4% of PC users that got infected with scareware think that File Recovery and similar applications are genuine Windows products designed to enhance system protection against viruses and system failures. Bit shocking isn't it.
Scareware infection symptoms are almost identical – fake scanners and misleading security alerts popping up at random intervals. Also, File Recovery is a very generic name and very competitive keyword at the same time. The last one was called Data Recovery. Cyber crooks choose very competitive keywords as their bogus software names making it hard to rank well in search results. It’s a wise move but users will probably search for File Recovery virus or malware or anything like that and we are pretty sure that Google will handle everything just fine.
Cyber crooks use various techniques like spam; drive-by downloads, and fake virus scanners to distribute rogue security applications. Even thought, most of the reports show that Fake AV applications seem to be on decline, they are still a significant threat. There are still many active scareware distribution channels and affiliate networks called ‘partnerka.’ The rules are different now. Two or more years ago, cyber crooks that were promoting scareware earned ~$25 per sale or sometimes even more. Now, they can earn $50 and more. 10k infected machines per day adds additional 10% revenue share. But yeah, in the last few months, there hasn't been much to talk about.
This rogue HDD repair program hides certain files, usually shortcuts and Desktop icons, and moves other files to Windows %Temp%\smtmp folder.
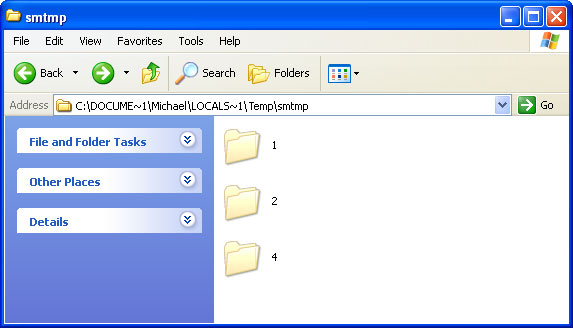
Do not delete any files from your Temp folder. We will show you how to restore hidden files in the removal guide below.
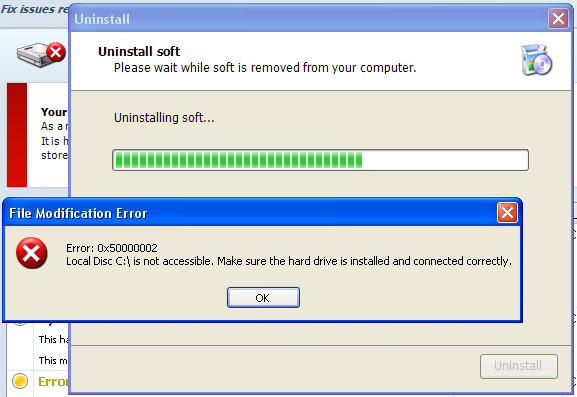
Certain fake security applications as well as fake PC repair utilities use very aggressive methods to scare users into believing that their computer are badly infected or damaged while others show up every ten minutes or so and remind you about security issues that need your attention. Recent scareware variants had working uninstallers, so levels of aggressive behavior are clearly different. Unfortunately, File Recovery malware uninstall doesn't work. You can find the uninstaller in your "All Programs" list. Clicking uninstall button calls a fake system error (see the image below). The rogue application claims that you cannot uninstall it because your local disk is not accessible. The funny thing is, you can uninstall whatever program you want but not this one. Coincidence? :) Of course not.
File Recovery removal is relatively easy unless it comes bundled with sophisticated malicious software, very often the ZeroAccess rootkit. When running, the rogue application blocks access to Web pages by showing a warning message in the browser and shuts download running antivirus software. But don’t worry there’s definitely a way to remove File Recovery virus. Scroll down a bit for step-by-step removal instructions. If you need help removing this malware from your PC, please let me know (leave a comment below). Good luck!
Source: http://deletemalware.blogspot.com
Quick File Recovery malware removal:
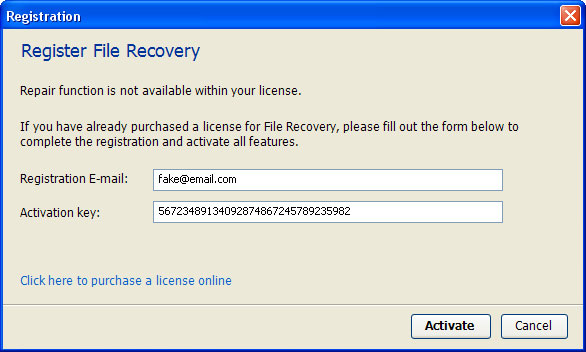
1. Use the activation key given below to register your copy of File Recovery malware. This will allow you to download and run recommended malware removal software and automatically restore hidden files and shortcuts. Don't worry, you're not doing anything illegal. Select "Trial version. Click to activate" (at the bottom of the fake scanner screen). Use fake email and the following activation key:
fake@mail.com
56723489134092874867245789235982
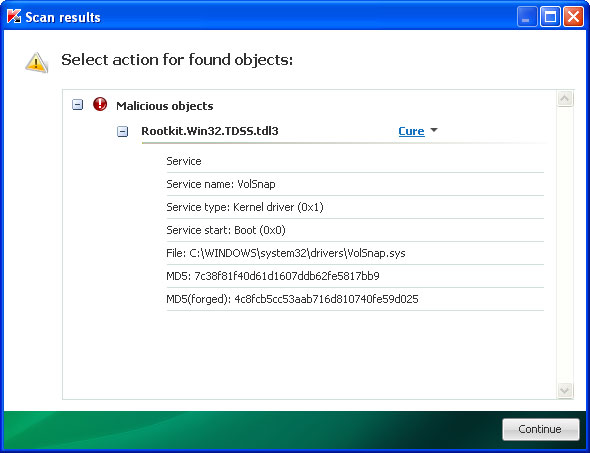
2. Download TDSSKiller and run a system scan. Remove found rootkits (if any). Reboot your computer if required.
3. Download recommended anti-malware software (direct download) and run a full system scan to remove this virus from your computer.
Alternate "File Recovery" removal instructions:
1. First of all, you need to unhide the files and folders. Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter cmd and hit Enter or click OK.
At the command prompt, enter attrib -h /s /d and hit Enter. Now, you should see all your files and folders. NOTE: you may have to repeat this step because the malware may hide your files again.
If you still can't see any of your files, Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter explorer and hit Enter or click OK.
2. Open Internet Explorer. Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter iexplore.exe and hit Enter or click OK.
Open Internet Explorer and download TDSSKiller. This malware usually (but not always) comes bundled with TDSS rootkit. Removing this rootkit from your computer is very important (if exists). Run TDSSKiller to remove the rootkit.
3. Finally, download recommended anti-malware software (direct download) to remove this virus from your computer.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
Manual File Recovery removal instructions:
1. First of all, you need to unhide the files and folders. Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter cmd and hit Enter or click OK.

At the command prompt, enter attrib -h /s /d and hit Enter. Now, you should see all your files and folders. NOTE: you may have to repeat this step because the malware may hide your files again.

2. The rogue application will place an icon or your desktop. Right click on the icon, click Properties in the drop-down menu.
Then click the Shortcut tab.
The location of the malware is in the Target box.
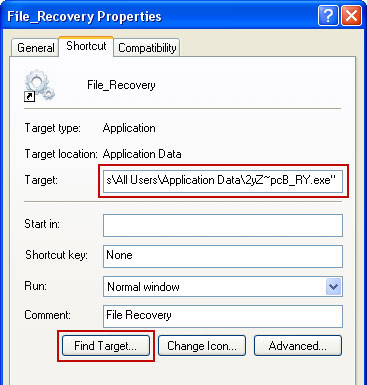
On computers running Windows XP, malware hides in:
C:\Documents and Settings\All Users\Application Data\
On computers running Windows Vista/7, malware hides in:
C:\ProgramData\
NOTE: by default, Application Data folder is hidden. Malware files are hidden as well. To see hidden files and folders, please read Show Hidden Files and Folders in Windows.
3. Click "Find Target..." button, it will take you to the folder where the malicious files are located. Or you can simply browse to those files manually.
Example Windows XP:
C:\Documents and Settings\All Users\Application Data\2yZ~pcB_RY.exe
Example Windows Vista/7:
C:\ProgramData\2yZ~pcB_RY.exe
Basically, there will be a couple of files named with a series of numbers or letters.
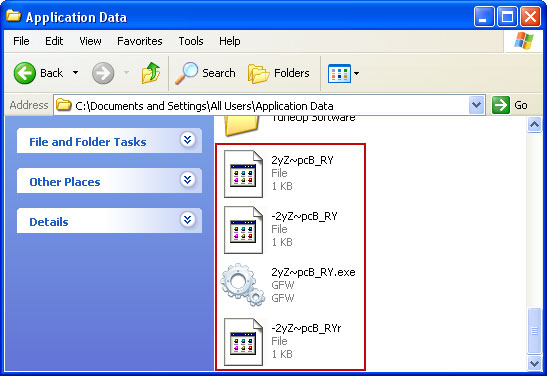
For example, rename 2yZ~pcB_RY.exe to virus.vir and click Yes to change it. Please note, your file name will probably be different.
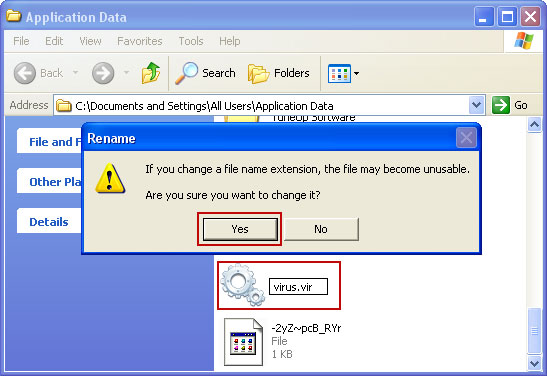
It should be: C:\Documents and Settings\All Users\Application Data\virus.vir
Instead of: C:\Documents and Settings\All Users\Application Data\2yZ~pcB_RY.exe
4. Restart your computer. The malware should be inactive after the restart.
5. Open Internet Explorer and download TDSSKiller.This malware usually (but not always) comes bundled with TDSS rootkit. Removing this rootkit from your computer is very important (if exists). Run TDSSKiller and remove the rootkit.

6. Download recommended anti-malware software (direct download) to remove this virus from your computer
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
Associated File Recovery files and registry values:
Files:
Windows XP:
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Desktop\File Recovery.lnk
- %UsersProfile%\Start Menu\Programs\File Recovery\
- %UsersProfile%\Start Menu\Programs\File Recovery\File Recovery.lnk
- %UsersProfile%\Start Menu\Programs\File Recovery\Uninstall File Recovery.lnk
%UserProfile% refers to: C:\Documents and Settings\[User Name]
Windows Vista/7:
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Desktop\File Recovery.lnk
- %UsersProfile%\Start Menu\Programs\File Recovery\
- %UsersProfile%\Start Menu\Programs\File Recovery\File Recovery.lnk
- %UsersProfile%\Start Menu\Programs\File Recovery\Uninstall File Recovery.lnk
%UserProfile% refers to: C:\Users\[User Name]
Registry values:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS].exe"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS]"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = '/{hq:/s`s:/ogn:/uyu:/dyd:/c`u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/`wh:/lqf:/lqdf:/lnw:/lq2:/l2t:/v`w:/rbs:'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "CheckExeSignatures" = 'no'
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = 'yes'
No comments:
Post a Comment