File Restore malware GUI
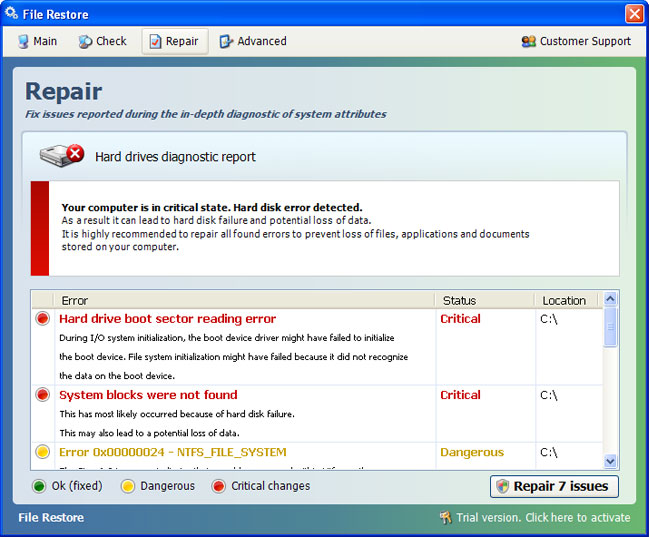
Suddenly appearing "Serious Disk Error" pop-ups and fake system notifications are the main symptoms of "File Restore" malware sales program infection. There are many variations of fake security alerts such as: "hard drive controller failure", "device initialization failed" and many more. Clicking on fake alerts opens up only the "File Restore" program which you obviously didn't install. The rogue repair tool has this amazingly fast auto-scan mode which detects and displays non-existent had drive reading errors, RAM failures and other supposedly critical system errors. After an auto-scan, "Repair 7 issues" opens up a convenient means to order a fix from this service or to "activate" the repair by purchasing the bogus program.
What is more, to motivate purchase, all icons and shortcuts have been wiped from the Start Menu, Desktop and from the list if most recently used programs. Now comes the important part, DO NOT delete files from your Temp folder or use any temp file cleaners. I know most of you guys use file cleaners to remove malware remnants and unnecessary files. But this time, DON'T! The rogue program moves certain fails to Windows Temp folder, specifically %Temp%\smtmp. Normally, you'll see something like this in your Temp folder. Note, that this folder is hidden.
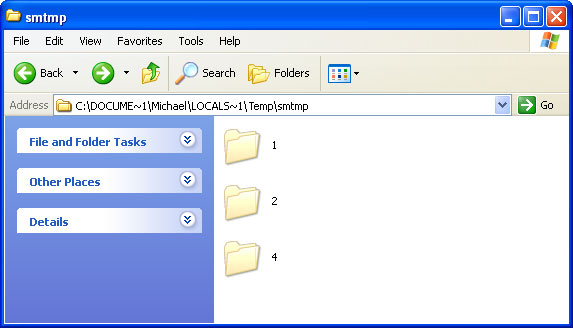
So, even though, it now appears as if all your files are gone they are actually still there. It's just you can't see them. Deleting "File Restore" malware files manually won't solve the problem, because they are just the tip of an iceberg. You need to restore your files first and only then remove core elements of this malware using recommended anti-malware software. To remove this malicious software and restore your files safely, please follow the removal instructions below. If you have any further questions please let us know - we will be happy to assist you. Good luck and be safe online!
Quick "File Restore" malware removal:
1. Use the activation key given below to register your copy of File Restore malware. This will allow you to download and run recommended malware removal software and automatically restore hidden files and shortcuts. Don't worry, you're not doing anything illegal and it won't make the situation worse. Select "Trial version. Click to activate" (at the bottom right hand corner of the fake scanner screen).
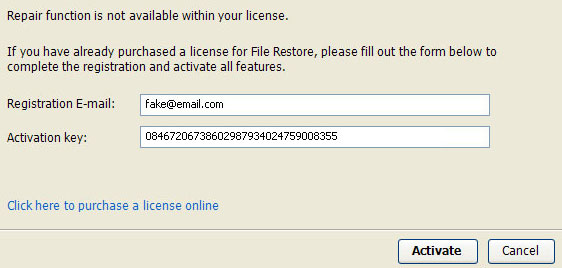
Use fake email and the following activation key:
Registration E-mail: fake@mail.com
Activation key: 08467206738602987934024759008355
2. Download TDSSKiller and run a system scan. Remove found rootkits (if any). Reboot your computer if required.
3. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
Alternate "File Restore" removal instructions:
1. First of all, you need to unhide the files and folders. Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter cmd and hit Enter or click OK.
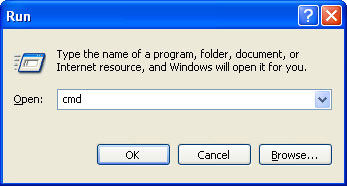
At the command prompt, enter attrib -h /s /d and hit Enter. Now, you should see all your files and folders. NOTE: you may have to repeat this step because the malware may hide your files again.
Open Internet Explorer. If the shortcut is hidden, pelase Select Run... from the Start Menu or just hit the key combination CTRL+R on your keyboard. In the Open: field, enter iexplore.exe and hit Enter or click OK.

2. Download and run this utility to restore missing icons and shortcuts.
3. Now, please download TDSSKiller and run a system scan. Remove found rootkits as shown in the image below. Reboot your computer if required.
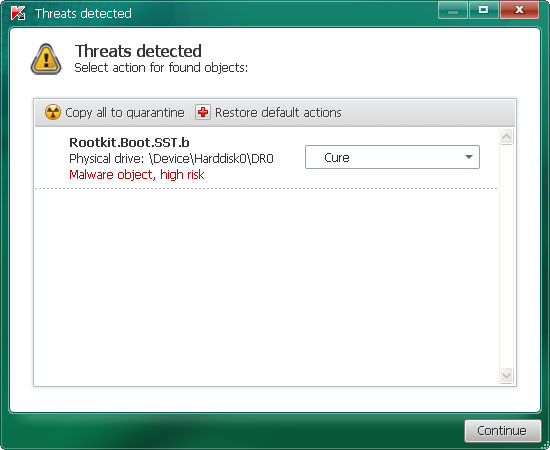
Please note that your computer might be rootkit free, not all version of "File Restore" comes bundled with rootkits. Don't worry if TDSSKiller didn't find a rootkit.
4. Finally, download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this malicious software from your computer.
NOTE: With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
5. The malicious software should be gone now. If certain icons and shortcuts are still missing, please use restoresm.zip.
Associated "File Restore" files and registry values:
Files:
Windows XP:
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\Application Data\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Desktop\File Restore.lnk
- %UsersProfile%\Start Menu\Programs\File Restore\
- %UsersProfile%\Start Menu\Programs\File Restore\File Restore.lnk
- %UsersProfile%\Start Menu\Programs\File Restore\Uninstall File Restore.lnk
%UserProfile% refers to: C:\Documents and Settings\[User Name]
Windows Vista/7:
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS]
- %AllUsersProfile%\[SET OF RANDOM CHARACTERS].exe
- %UsersProfile%\Desktop\File Restore.lnk
- %UsersProfile%\Start Menu\Programs\File Restore\
- %UsersProfile%\Start Menu\Programs\File Restore\File Restore.lnk
- %UsersProfile%\Start Menu\Programs\File Restore\Uninstall File Restore.lnk
%UserProfile% refers to: C:\Users\[User Name]
Registry values:
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = 'Yes'
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = "Yes"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "CertificateRevocation" = '0'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnonBadCertRecving" = '0'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop "NoChangingWallPaper" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = '.zip;.rar;.nfo;.txt;.exe;.bat;.com;.cmd;.reg;.msi;.htm;.html;.gif;.bmp;.jpg;.avi;.mpg;.mpeg;.mov;.mp3;.m3u;.wav;.scr;'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer "NoDesktop" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "<random>.exe"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "<random>"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "DisableTaskMgr" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "CheckExeSignatures" = 'no'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "Hidden" = '0'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "ShowSuperHidden" = '0'
No comments:
Post a Comment