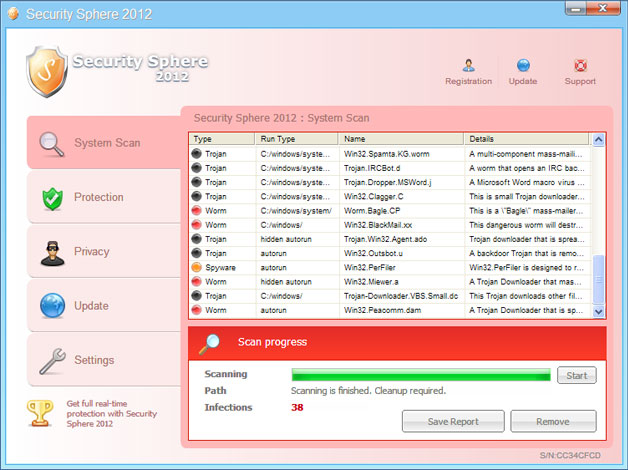
Here are some sceenshots of fake security alerts generated by Security Sphere 2012:
Warning: Your computer is infected
Detected spyware infection!
Click this message to install the last update of security software...

Warning!
Application cannot be executed. The file taskmgr.exe is infected.
Please activate your antivirus software.

Security Sphere 2012 Firewall Alert
Security Sphere 2012 has blocked a program from accessing the internet
Internet Explorer Internet browser is infected with worm Lsas.Blaster.Keyloger.

Security Sphere 2012
WARNING! 38 infections found!!!

Rogue AVs face survival challenges just like any other type of malicious software. Security Sphere 2012 drops a rootkit from the TDSS family. The rootkit must be removed; otherwise, the rogue program will be re-downloaded onto your computer. Thankfully, there's a tool called TDSSKiller which is designed to remove TDL3/4 and other rootkits from infected computer. For more informarion, please see the removal instructions below. If for any reasons you can't disable Security Sphere 2012 and run anti-malware software, you can activate the rogue program and disable the restrictions.
1. Please enter the following code: 8945315-6548431.

2. Once this is done, you are free to install recommended anti-malware software (Spyware Doctor) and remove the rogue anti-virus program from your computer properly.
Finally, if you have already purchased this fake security application, please contact your credit card company and dispute the charges. Please note that you may become a victim of credit card scam or even identity theft. Compute wisely!
Security Sphere 2012 removal instructions:
1. Please reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
Alternate Security Sphere 2012 removal instructions:
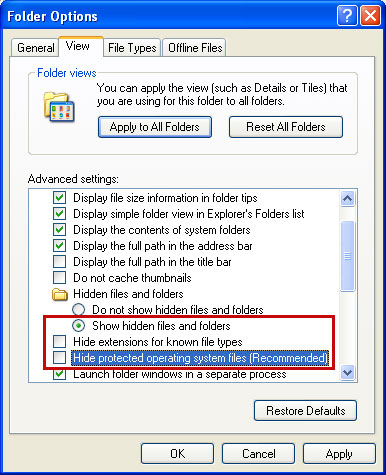
Make sure that you can see hidden and operating system protected files in Windows. For more in formation, please read Show Hidden Files and Folders in Windows.
Under the Hidden files and folders section, click Show hidden files and folders, and remove the checkmarks from the checkboxes labeled:
- Hide extensions for know file types
- Hide protected operating system files
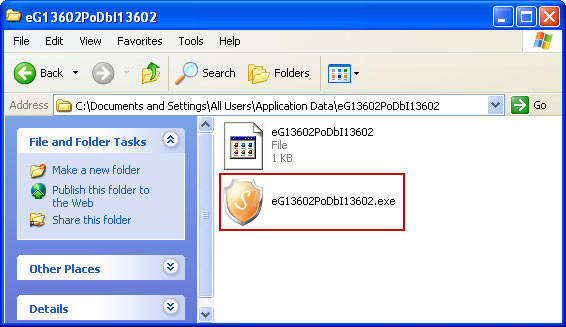
1. Find Security Sphere 2012 file(s).
On computers running Windows XP, malware hides in:
C:\Documents and Settings\All Users\Application Data\
On computers running Windows Vista/7, malware hides in:
C:\ProgramData\
2. Look for malicious files in the given directories depending on the Windows version you have.
Example Windows XP:
C:\Documents and Settings\All Users\Application Data\eG13602PoDbI13602.exe
Example Windows Vista/7:
C:\ProgramData\eG13602PoDbI13602.exe
Basically, there will be a malicious ".exe" file named with a series of numbers or letters.
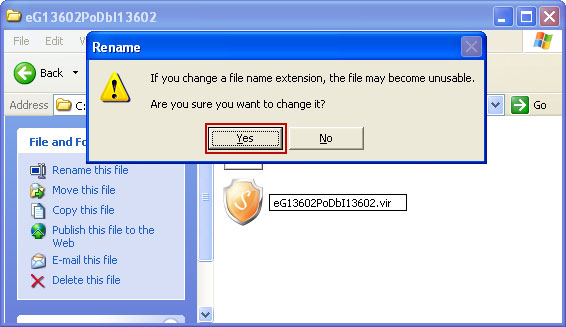
Rename eG13602PoDbI13602.exe to eG13602PoDbI13602.vir. Here's an example:
3. Restart your computer. After a reboot, Security Sphere 2012 won't start and you will be able to run anti-malware software.
4. Open Internet Explorer. Download exe_fix.reg and run it. Click "Yes" to safe the changes.
5. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
Security Sphere 2012 removal video:
Associated Security Sphere 2012 files and registry values:
Files:
Windows XP:
- C:\Documents and Settings\All Users\Application Data\[SET OF RANDOM CHARACTERS].exe
- C:\ProgramData\[SET OF RANDOM CHARACTERS].exe
- HKEY_USERS\.DEFAULT\Software\Microsoft\Internet Explorer\Main\featurecontrol\FEATURE_BROWSER_EMULATION "svchost.exe"
- HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings "enablehttp1_1" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce "[SET OF RANDOM CHARACTERS]"
No comments:
Post a Comment